TryHackMe! Thompson
- Srivathsa Dhanvantri
- Aug 24, 2020
- 3 min read
TryHackMe is an online platform that teaches Cybersecurity through hands-on virtual labs. Whether you are an expert or beginner, learn through a virtual room structure to understand theoretical and practical security elements.
Thompson is an easy room on TryHackMe for beginners to explore.
You have to first signup to join the room. There are few simple steps that you can follow in the Signup page. Next follow the steps in the Welcome room to configure the VPN connectivity.
I have connected to TryHackMe network using OpenVPN on Kali Linux. Once you connect, the access page will confirm the status by confirming your IP address and status. Join the room to access it's contents.

Click on Deploy to start the Vulnerable target machine.

The IP address of the target is displayed.
Start Enumeration using nmap. The -sV option will do a service fingerprinting too.

We can see that the nmap scan has revealed that port 22 and port 8080 are open. Open SSH is running on port 22 and Apache Tomcat is running on port 8080.
Explore the Apache Tomcat service using a web browser.

The home page of the Apache Tomcat could be seen. Run nikto scan to check for vulnerabilities.

There are many vulnerabilities found, Default account for Tomcat Manager is also found in the nikto scan. Also run gobuster to scan for directories under this URL.

The gobuster too revealed the manager page. Visit the /manager page.
We can see the default credentials for manager-gui on this page.

Try to login into the manager-gui using this credentials.

You can also run user enumeration scan for Metasploit.
Open msfconsole and search for tomcat. A number of options will appear.


Select the 9th option in the list. That is index 8. so the command would be use 8. Set the RHOST IP and RPORT number. That is Target host IP and Target port number.
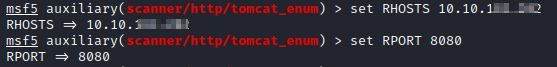
Set the target URI of host-manager. Then use the command run and check the users found by the scanner.

Since you already know the user tomcat and it's default password, you can run an exploit from Metasploit for manager upload.
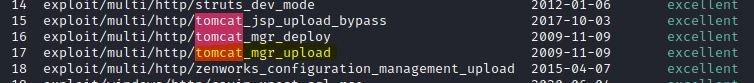
Select the tomcat_mgr_upload exploit by using the command use 17. The command show options will give you all the parameters that need to set in order for the exploit to work. set all these options as shown. Your RHOST and LHOST IP and port may vary. RHOST is the target host IP address and LHOST is the listening host(tun0 interface IP address on my Kali VM in my case).
Once all the options are set, use the command exploit

You have successfully obtained a meterpreter session. Run the command shell to get a CLI of the target host and use Python tty command as shown to get a more stable shell.

Navigate to the user's home directory to find the user flag.

Validate the user flag on TryHackMe.
Notice that there is a script in the user's home directory and probably that is utilized by root as well. Try updating the script with your own command to escalate the privilege of current user.

I am just updating a command in script to just copy the contents of root.txt to the user's home directory. Whereas you can try updating the script to give you a root shell.
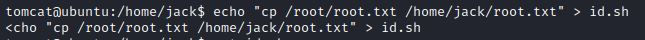
After a while the root.txt appeared on user's home directory.

Validate the flag on TryHackMe.

I hope this write-up was informative for you. Please leave a feedback. Thank you
-Srivathsa Dhanvantri
Commentaires